Applying IRSA
To use IAM roles for service accounts in your cluster, an IAM OIDC Identity Provider must be created and associated with a cluster. An OIDC has already been provisioned and associated with your EKS cluster:
Go to the Identity Providers in IAM Console:
https://console.aws.amazon.com/iamv2/home#/identity_providers
You will see an OIDC provider has created for your EKS cluster:
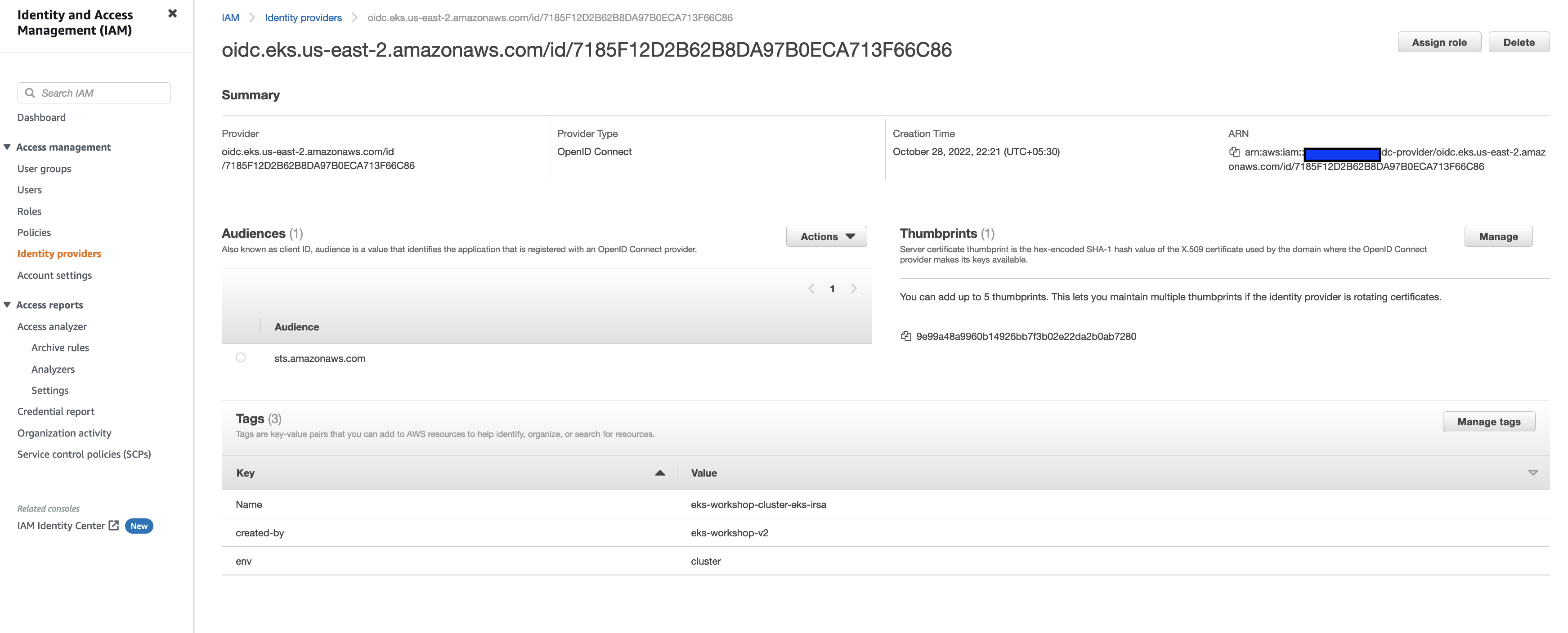
Another option is to use AWS CLI to verify the IAM OIDC Identity Provider.
{"OpenIDConnectProviderList": [
{"Arn": "arn:aws:iam::012345678901:oidc-provider/oidc.eks.us-east-2.amazonaws.com/id/7185F12D2B62B8DA97B0ECA713F66C86"
}
]
}
And validate its association with our Amazon EKS cluster.
{ "oidc": {"issuer": "https://oidc.eks.us-west-2.amazonaws.com/id/7185F12D2B62B8DA97B0ECA713F66C86"
}
}
An IAM role which provides the required permissions for the carts service to read and write to DynamoDB table has been created for you. You can view the policy like so:
{"Statement": [
{"Action": "dynamodb:*",
"Effect": "Allow",
"Resource": [
"arn:aws:dynamodb:us-west-2:1234567890:table/eks-workshop-carts",
"arn:aws:dynamodb:us-west-2:1234567890:table/eks-workshop-carts/index/*"
],
"Sid": "AllAPIActionsOnCart"
}
],
"Version": "2012-10-17"
}
The role has also been configured with the appropriate trust relationship which allows the OIDC provider associated with our EKS cluster to assume this role as long as the subject is the ServiceAccount for the carts component. You can view it like so:
{"Version": "2012-10-17",
"Statement": [
{"Sid": "",
"Effect": "Allow",
"Principal": {"Federated": "arn:aws:iam::1234567890:oidc-provider/oidc.eks.us-west-2.amazonaws.com/id/22E1209C76AE64F8F612F8E703E5BBD7"
},
"Action": "sts:AssumeRoleWithWebIdentity",
"Condition": { "StringEquals": {"oidc.eks.us-west-2.amazonaws.com/id/22E1209C76AE64F8F612F8E703E5BBD7:sub": "system:serviceaccount:carts:carts"
}
}
}
]
}
All thats left is to re-configure the Service Account object associated with the carts application adding the required annotation to it, so IRSA can provide the correct authorization for Pods using the IAM Role above.
Let's validate the SA associated with the carts Deployment.
Service Account: cart
Now lets check the value of CARTS_IAM_ROLE which will provide the ARN of the IAM Role for the Service Account annotation.
arn:aws:iam::1234567890:role/eks-workshop-carts-dynamo
Once we've verified the IAM Role to be used, we can run Kustomize to apply the change on the Service Account.
- Kustomize Patch
- ServiceAccount/carts
- Diff
apiVersion: v1
kind: ServiceAccount
metadata:
name: carts
namespace: carts
annotations:
eks.amazonaws.com/role-arn: $(CARTS_IAM_ROLE)
apiVersion: v1
kind: ServiceAccount
metadata:
annotations:
eks.amazonaws.com/role-arn: arn:aws:iam::1234567890:role/eks-workshop-carts-dynamo
name: carts
namespace: carts
apiVersion: v1
kind: ServiceAccount
metadata:
+ annotations:
+ eks.amazonaws.com/role-arn: arn:aws:iam::1234567890:role/eks-workshop-carts-dynamo
name: carts
namespace: carts
Validate if the Service Account was annotated.
Annotations: eks.amazonaws.com/role-arn: arn:aws:iam::1234567890:role/eks-workshop-carts-dynamo
With the ServiceAccount updated now we just need to recycle the carts Pod so it picks it up:
deployment.apps/carts restarted